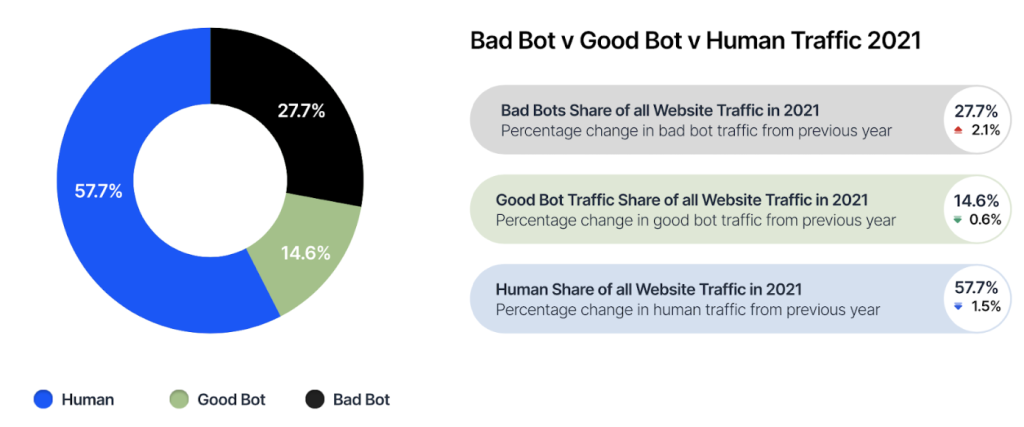
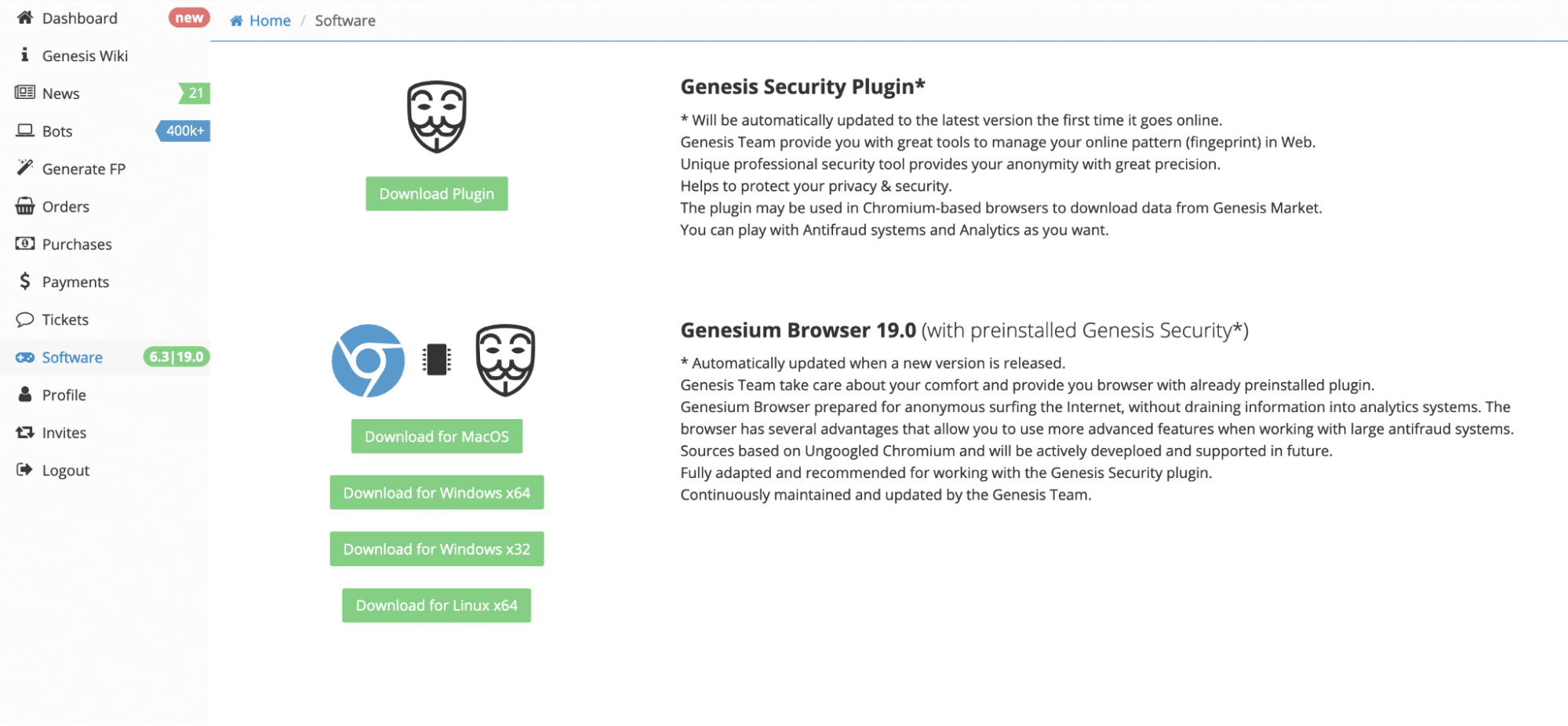
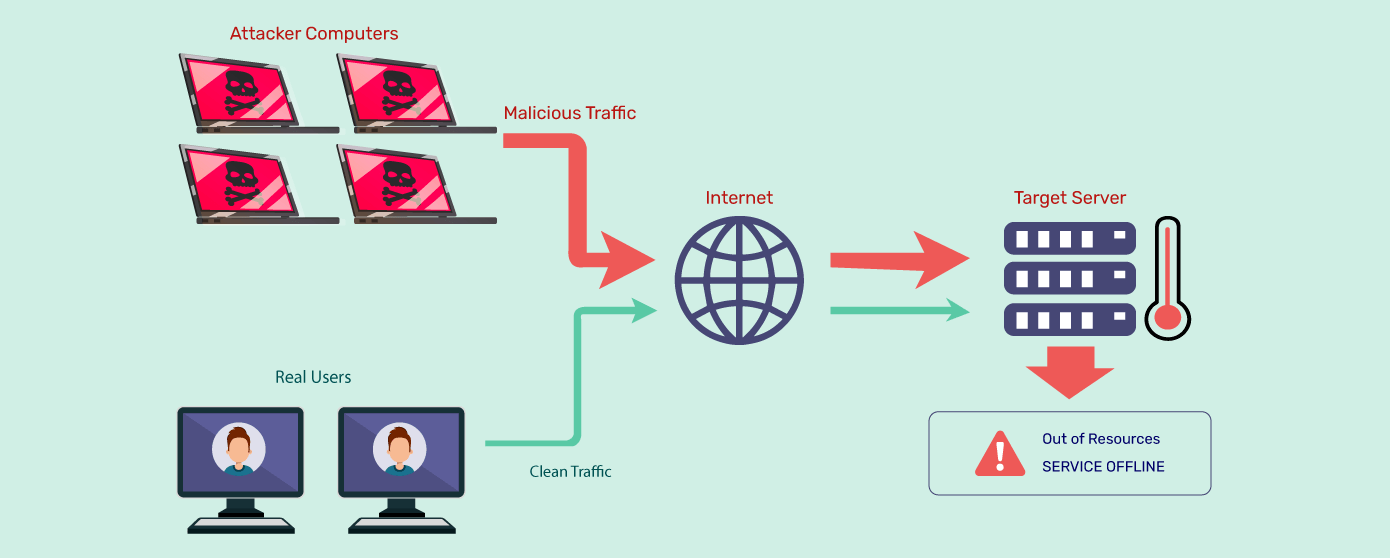
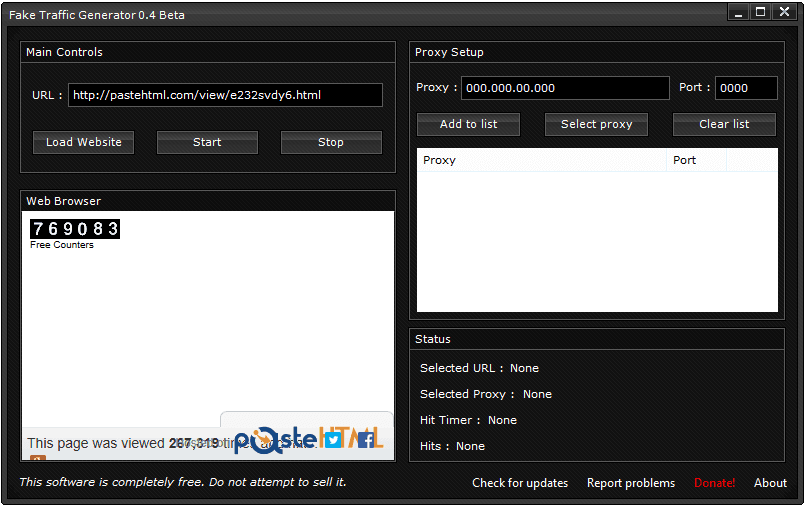
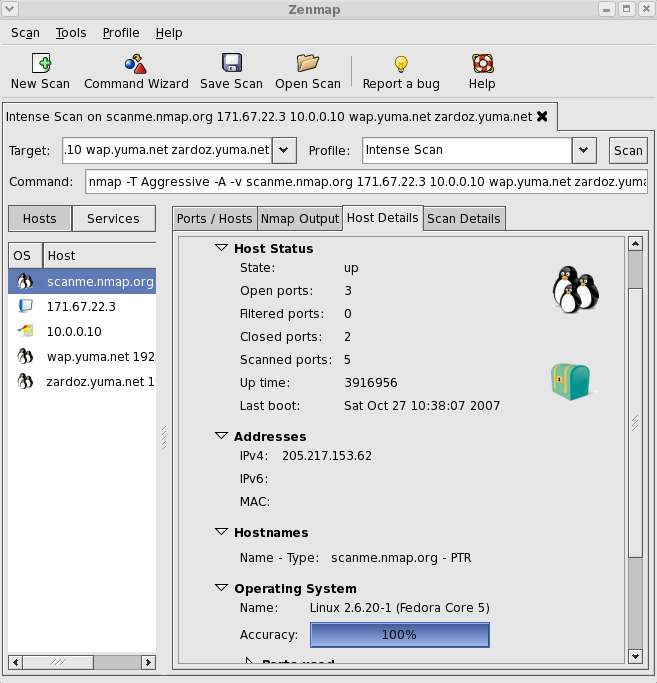
Gregg Gonsalves on Twitter: "I would just never, ever condone something like this, 'cause it would be just wrong, and you'd be breakin' the law... https://t.co/5aEHMMxLp1" / Twitter
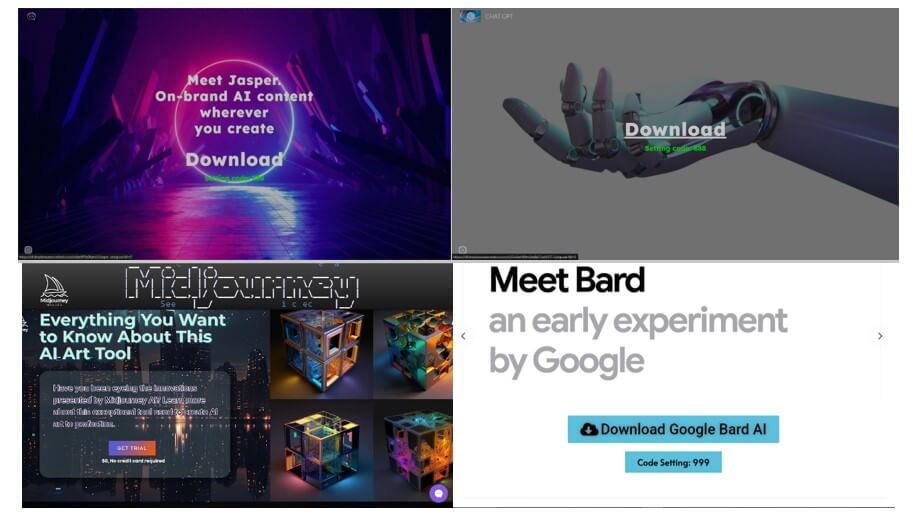
Facebook Flooded with Ads and Pages for Fake ChatGPT, Google Bard and other AI services, Tricking Users into downloading Malware - Check Point Blog

How Dare They Peep into My Private Life?”: Children's Rights Violations by Governments that Endorsed Online Learning During the Covid-19 Pandemic | HRW

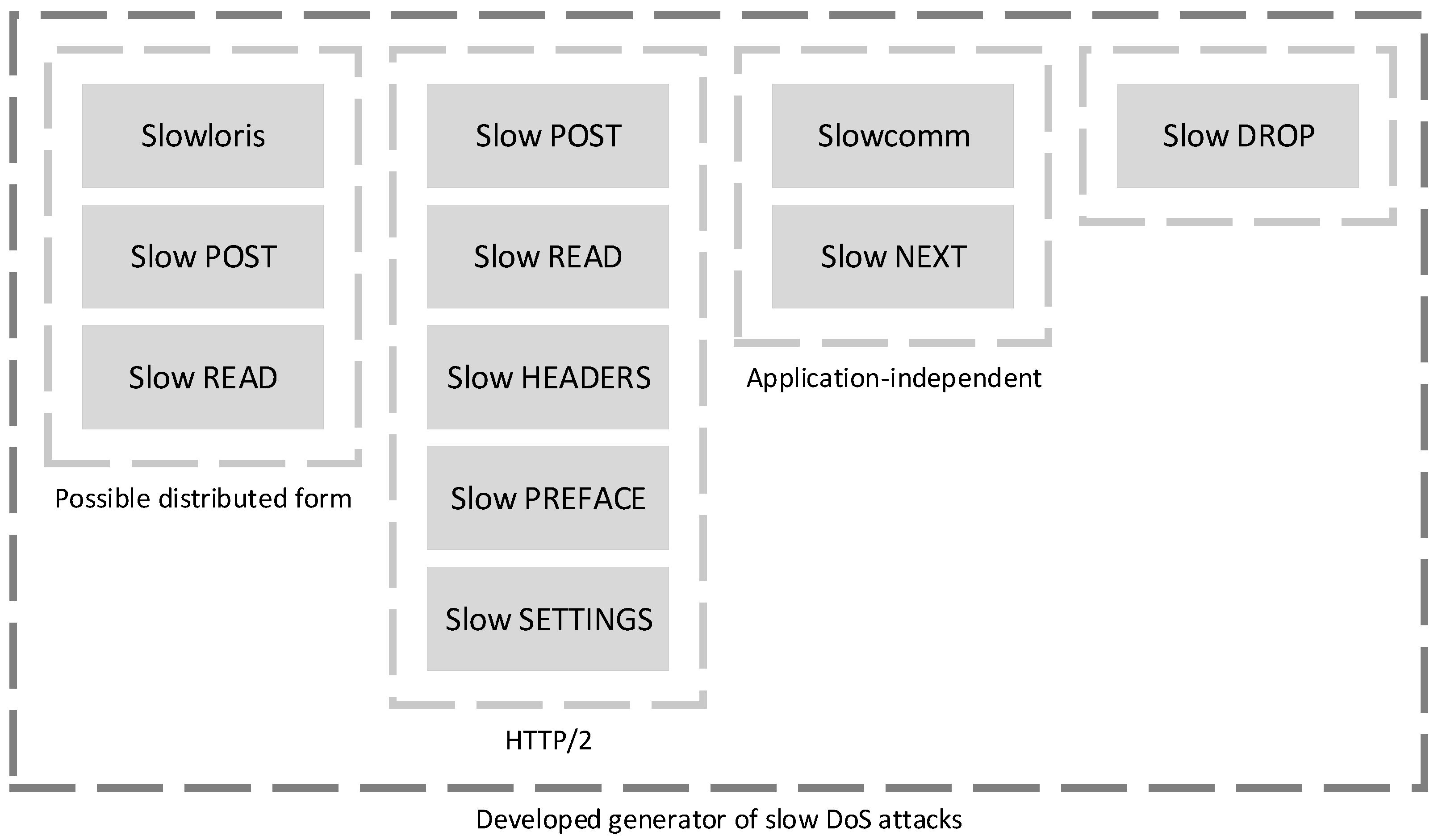
Sensors | Free Full-Text | SGAN-IDS: Self-Attention-Based Generative Adversarial Network against Intrusion Detection Systems

Modeling of cyber threat analysis and vulnerability in IoT-based healthcare systems during COVID - ScienceDirect
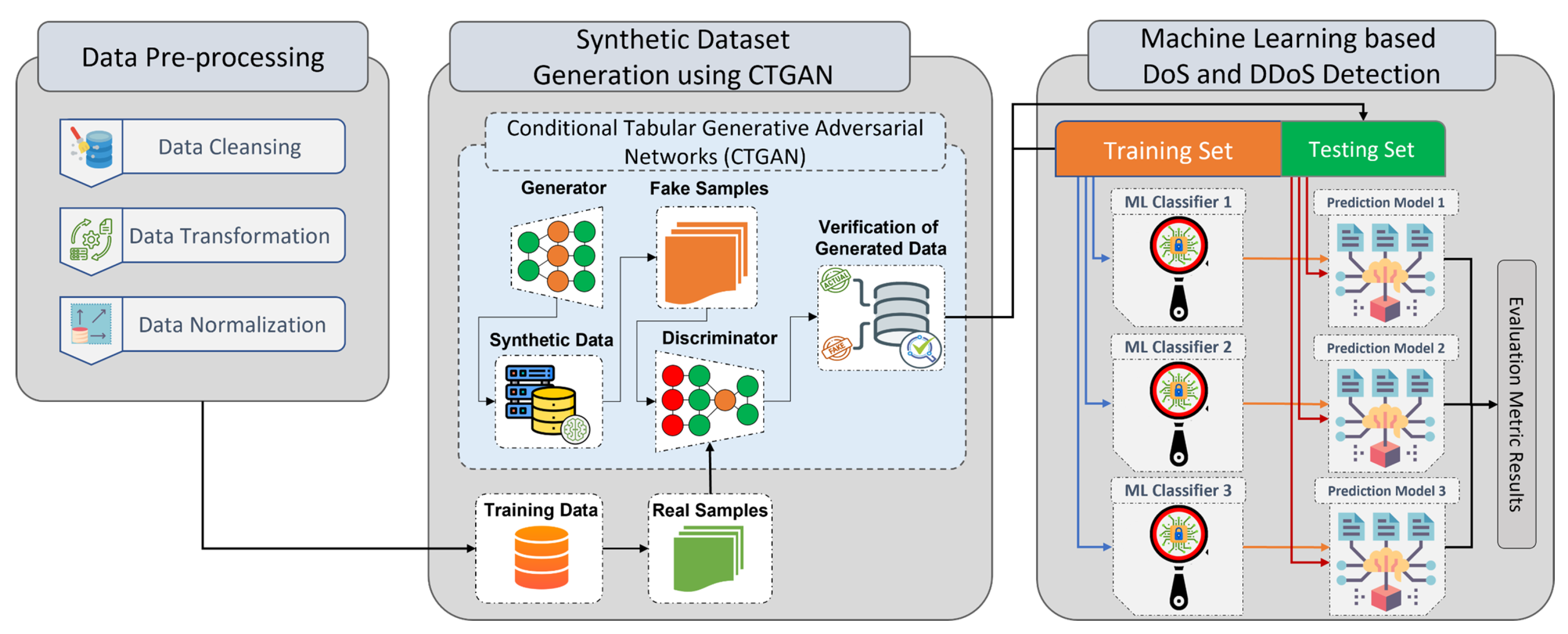
Sensors | Free Full-Text | Conditional Tabular Generative Adversarial Based Intrusion Detection System for Detecting Ddos and Dos Attacks on the Internet of Things Networks
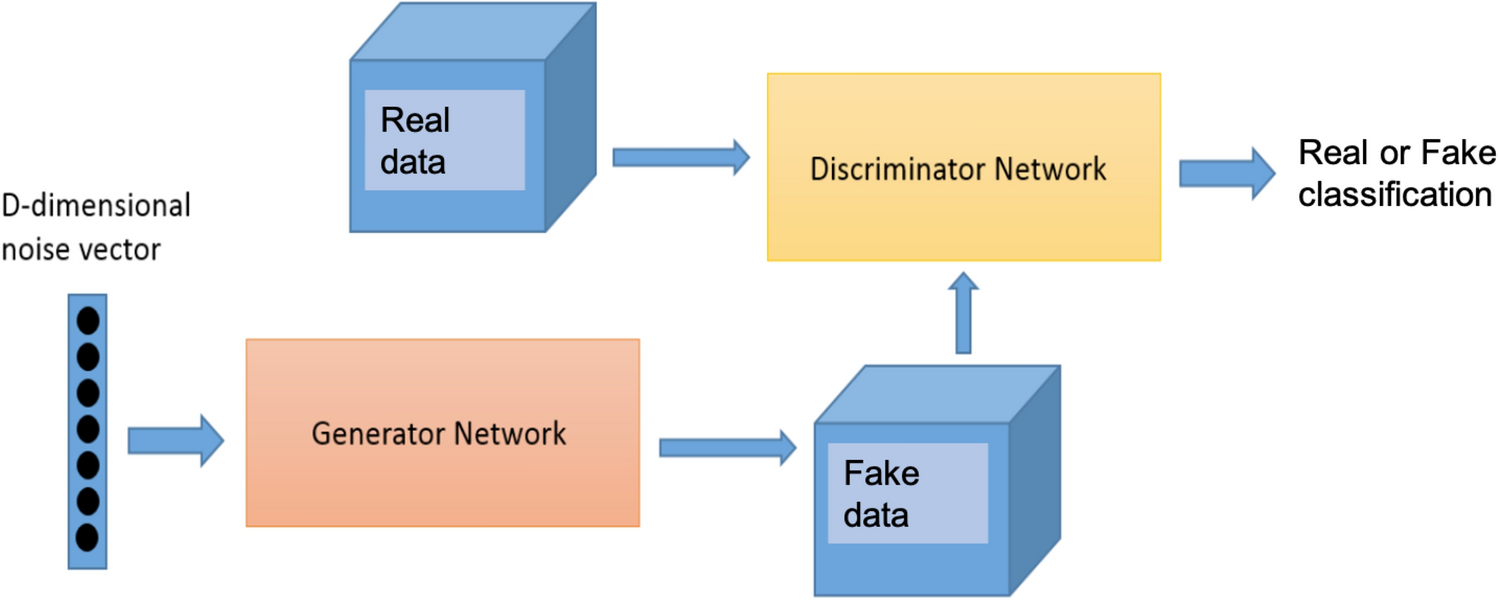
Synthetic flow-based cryptomining attack generation through Generative Adversarial Networks | Scientific Reports